INCIDENT REPORT: Mistery On CRO, Lazy Lion and CROugar Attack, Followed by Great Recovery
The full incident report on how one person simultaneously attacked 3 projects at once.
Incident Overview
On October 8th, 2024, Mistery On CRO, Lazy Lion, and CROugar Kingdom were attacked via a complete takeover of Discord permissions. The attacker impersonated Mistery on CRO founder, David, and shared a fake link to a supposed airdrop that was, in fact, a wallet drainer. Quick responses from the community helped limit the damage, with around $8,000 in direct financial losses, and no significant long-term impact on the affected projects.
Incident Summary
The attack was initiated through the psychological manipulation of Shadowbright, a member of the community. The attacker gained access to his Discord account, which allowed them to invite malicious bots, manipulate roles, and post wallet-draining links. Over the course of several hours, the attacker impersonated project founders and caused panic within the community. Fortunately, prompt intervention by moderators prevented more extensive damage.
Timeline of Events (UTC+2)
October 7th, 2024 [Time unknown]: Shadowbright was psychologically manipulated into clicking a malicious link, granting the attacker access to his Discord account.
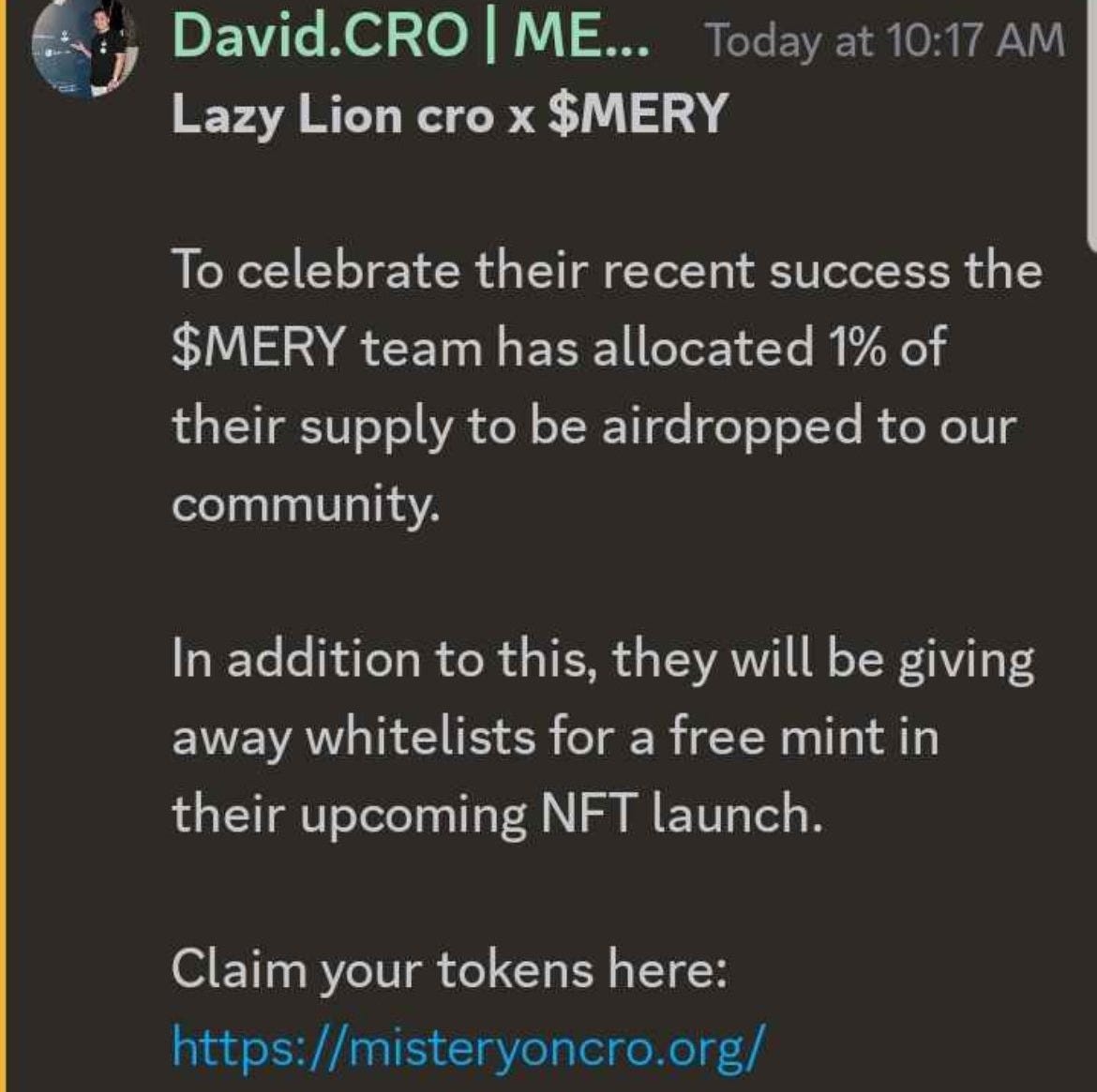
October 7th, 2024 [Time unknown]: The attacker registered the fake domain misteryoncro.org.
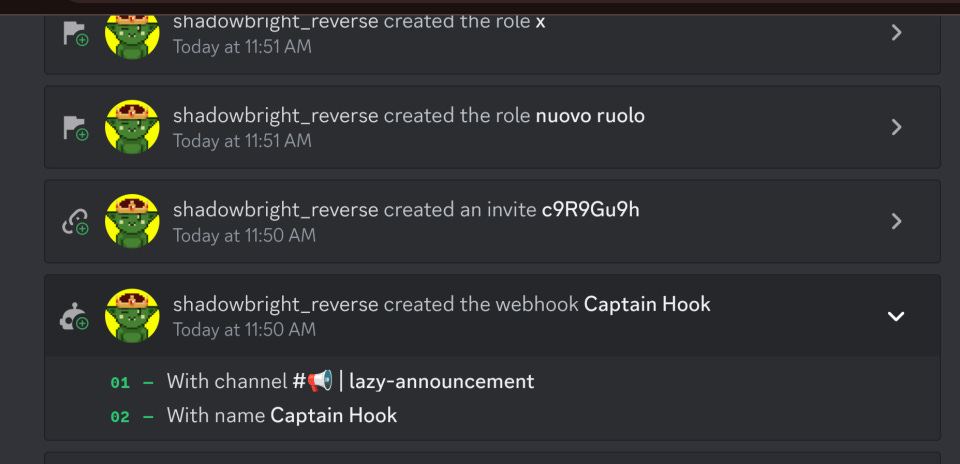
October 7th, 2024 [8:46 PM]: Using Shadowbright’s account, the attacker invited the Spidey Bot to the Mistery on CRO (MERY) Discord and created custom roles.
October 7th, 2024 [8:50 PM]: The attacker invited the Captain Hook Bot and set further custom roles in the MERY Discord.
October 8th, 2024 [1:17 AM]: The attacker, impersonating David CRO, shared a drainer link in the Mistery On CRO and Lazy Lion Discords, causing panic selling of MERY tokens.
October 8th, 2024 [1:20 AM]: The attacker posted the drainer link in the CROugar Kingdom Discord.
October 8th, 2024 [1:43 AM]: DreamQc alerted the community on X (formerly Twitter) about the drainer link.
October 8th, 2024 [~1:53 AM]: MERY moderators regained control of the Discord, removing the malicious link. At this time, the attacker sold 770,994,350 MERY for 102,272 WCRO ($8,032.78 USD) on Wolfswap.
October 8th, 2024 [2:42 AM]: The attacker transferred the stolen funds via SideShift to Ethereum, converting them to 3.21 ETH
October 8th, 2024 [2:48 AM - 2:53 AM]: The attacker split the funds into two parts and transferred 1.5 ETH each to the ChangeNOW exchange
October 8th, 2024 [8:27 AM]: Shadowbright shared his side of the story, explaining the initial compromise.
Impact Assessment
Five wallets were directly affected by the drainer link, leading to the following losses:
0x9bcb21a6310e48dde8abbcc68109df1fc1ed21ea: 549.999M MERY
0xc4e7e70a3a41c655b1b634da13dd2689af821616: 130.93M YOSHI + 4.435 SITH
0xca238f139800c145b83dd772f91b0abc715d0592: 220.995M MERY
0x76e001a9920a199cc07adfd080955c26949fc1e0: 0.85 MERY
0xbc08c8139b7d34a5afc80c9b319b1e50cd5e222a: 5.316k LOAF
Although only $8,032.78 worth of MERY was sold by the attacker, other stolen tokens remain in the attacker’s wallet.
Root Cause Analysis
The root cause of the attack was a combination of psychological manipulation and exploitation of Discord’s permissions system. Shadowbright was coerced into clicking a malicious link during a heated exchange with an imposter, allowing the attacker to gain control of his account. The attacker used this control to invite malicious bots and spread the wallet-draining link in various Discord servers.
Shadowbright’s Statement:
"Sorry guys… My Discord was hacked yesterday night. Fortunately, Discord is the only affected area. The hacker took advantage of my emotions during a heated conversation. They posted a link with fake 'proof' that we were scammers, and as a stupid mistake, I clicked on it. The hacker invited bots and gave them admin rights in the MERY Discord. Luckily, our dev quickly intervened."
Resolution & Mitigation
The attacker was banned from all affected Discords, and the compromised accounts were locked and reset.
Shadowbright's account was re-secured, with all access and permissions restored to the project moderators.
The Discord ID of the attacker (1240819312625848390) has been gathered to prevent future exploits.
Communication
The attack was communicated to the community on X and directly within Discord channels. Users were quickly informed about the compromised links, and efforts were made to restore order and calm within the affected communities.
Post-Incident Analysis
Lessons Learned: The importance of secure Discord practices, including 2FA and avoiding emotionally charged interactions with unknown parties, became clear. The need for rapid response and immediate community notifications was also reinforced.
Future Action Items: Implement stricter role permissions, require enhanced verification for Discord bots, and ensure key team members are available to respond to incidents at any time.
Impact on MERY: At the time of writing, the MERY community strongly recovered to the pre-attack, mainly due to the fact that most of the downside was caused by non-impacted users in panic sales.
Impact on LAZY: LAZY was not directly impacted by the attacker sell, but rather impacted by MERY due to the nature of LP pairing. However, the price has stabilized in the same way as MERY upon recovery
References & Attachments
Attacker's Wallet: Cronoscan
Attack on Cronos Overview: Metasleuth
Destination of Funds: Metasleuth
Our Incident Thread: Build On Cronos
Discord ID of the Attacker: 1240819312625848390
Conclusion
The attack on Mistery On CRO, Lazy Lion, and CROugar Kingdom highlights the importance of strong security protocols, especially in community-driven platforms like Discord. The incident stemmed from psychological manipulation, allowing the attacker to exploit permissions and spread a harmful wallet drainer. Fortunately, the quick response from the development team and community minimized the financial impact and prevented long-term damage to the projects.
Moving forward, stricter security measures such as enhanced bot verifications, role restrictions, and community education will be crucial in preventing similar incidents. The key takeaway from this event is the importance of vigilance and maintaining composure when dealing with unexpected accusations or suspicious links. By learning from this incident, the community can strengthen its defenses and build a more resilient ecosystem.










Very nice post, thx fam!